A new ransomware has been released that not only encrypts your files, but also deletes them if you take too long to make the ransom payment of $150 USD. The Jigsaw Ransomware, named after the iconic character that appears in the ransom note, will delete files every hour and each time the infection starts until you pay the ransom. At this time is currently unknown how this ransomware is distributed.
This is the first time that we have seen these types of threats actually being carried out by a ransomware infection. The good news is that a method has been discovered that allows victims to decrypt their files for free.

Jigsaw Ransomware is serious about its threats...
It is not the first time that we have seen ransomware threaten to delete files, but this is the first time that one has actually carried out its threats. The Jigsaw Ransomware deletes files every 60 minutes and when the program is restarted.
Every hour, the Jigsaw Ransomware will delete a file on your computer and increment a counter. Over time this counter will cause more than one file to be deleted every hour.
More destructive, though, is the amount of files that are deleted every time the ransomware starts. After the initial infection, when the ransomware it restarted, whether that be from a reboot or terminating the process, Jigsaw will delete a thousand, yes a thousand, files from the victim's computer.
This process is very destructive and obviously being used to pressure the victim into paying the ransom.
How to decrypt and remove the Jigsaw Ransomware
Thankfully, through the analysis of MalwareHunterTeam, DemonSlay335, and myself it was discovered that it is possible to decrypt this ransomware for free. Using this information, Demonslay335 has released a decryptor that can decrypt files encrypted by the Jigsaw Ransomware. To decrypt your files, the first thing that you should do is terminate the firefox.exe and drpbx.exe processes in Task Manager to prevent any further files from being deleted. You should then run MSConfig and disable the startup entry called firefox.exe that points to the %UserProfile%\AppData\Roaming\Frfx\firefox.exe executable.
Once you have terminated the ransomware and disabled its startup, let's proceed with decrypting the files. The first step is to download and extract the Jigsaw Decryptor from the following URL:
https://www.bleepingcomputer.com/download/jigsaw-decrypter/
Then double-click on the JigSawDecrypter.exe file to launch the program. When the program launches you will be greeted with a screen similar to the one below.
To decrypt your files simply select the directory and click on the Decrypt My Files button. If you wish to decrypt the whole drive, then you can select the C: drive itself. It is advised that you do not put a checkmark in the Delete Encrypted Files option until you have confirmed that the tool can properly decrypt your files.
When it has finished decrypting your files, the screen will appear as below.
Now that your files are decrypted, I suggest that you run an antivirus or anti-malware program to scan your computer for infections.
Is this ransomware just a game for the devs?
After MalwareHunterTeam analyzed further variants of the Jigsaw Ransomware, he brought up an interesting point. Do "They even care about the money or just want to play with people?" When analyzing the variants, it has been shown that they are coded to only execute after a certain date. For example, the Portuguese variant is hard coded to only run after April 6th 2016, while another was set to go off on March 23, 2016.
There is also a wide range of ransom prices being offered, with prices ranging from $20 to 200 USD. Are these people motivated by money or is this just one big game to them?
Jigsaw Ransomware Technical Details
When the Jigsaw ransomware is launched it will scan your drives for certain file extension, encrypt them using AES encryption, and append a .FUN, .KKK, .GWS, or, .BTC extension to the filename depending on the version. The files targeted by the Jigsaw ransomware are:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp , .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .c, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .Qbw, .QBB, .QBM, .QBI, .QBR , .Cnt, .Des, .v30, .Qbo, .Ini, .Lgb, .Qwc, .Qbp, .Aif, .Qba, .Tlg, .Qbx, .Qby , .1pa, .Qpd, .Txt, .Set, .Iif , .Nd, .Rtp, .Tlg, .Wav, .Qsm, .Qss, .Qst, .Fx0, .Fx1, .Mx0, .FPx, .Fxr, .Fim, .ptb, .Ai, .Pfb, .Cgn, .Vsd, .Cdr, .Cmx, .Cpt, .Csl, .Cur, .Des, .Dsf, .Ds4, , .Drw, .Dwg.Eps, .Ps, .Prn, .Gif, .Pcd, .Pct, .Pcx, .Plt, .Rif, .Svg, .Swf, .Tga, .Tiff, .Psp, .Ttf, .Wpd, .Wpg, .Wi, .Raw, .Wmf, .Txt, .Cal, .Cpx, .Shw, .Clk, .Cdx, .Cdt, .Fpx, .Fmv, .Img, .Gem, .Xcf, .Pic, .Mac, .Met, .PP4, .Pp5, .Ppf, .Xls, .Xlsx, .Xlsm, .Ppt, .Nap, .Pat, .Ps, .Prn, .Sct, .Vsd, .wk3, .wk4, .XPM, .zip, .rar When encrypting a file it will add the filename to a list of encrypted files located at %UserProfile%\AppData\Roaming\System32Work\EncryptedFileList.txt. It will also assign a bitcoin address and save it in the %UserProfile%\AppData\Roaming\System32Work\Address.txt file.
Finally, Jigsaw will set an autorun that starts ransomware each time you login to Windows. Unfortunately, each time the ransomware starts, it will also delete 1,000 of the encrypted files.
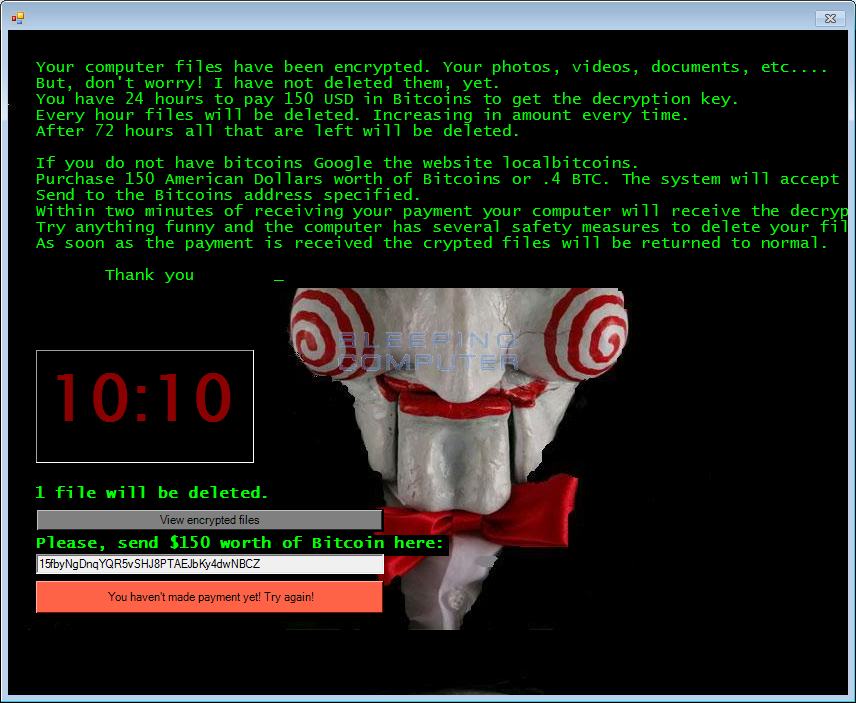
In the ransom note there is a 60 minute timer that counts down to 0. When it reaches 0 it will delete a certain amount of files depending on how many times the counter has reset. Each time it resets, a counter will increase, which will cause more files to be deleted on the next reset.
The text of the ransom notes we have seen are listed below. A big thanks to MalwareHunterTeam for keeping track of these.
Your computer files have been encrypted. Your photos, videos, documents, etc....
But, don't worry! I have not deleted them, yet.
You have 24 hours to pay 150 USD in Bitcoins to get the decryption key.
Every hour files will be deleted. Increasing in amount every time.
After 72 hours all that are left will be deleted.
If you do not have bitcoins Google the website localbitcoins.
Purchase 150 American Dollars worth of Bitcoins or .4 BTC. The system will accept either one.
Send to the Bitcoins address specified.
Within two minutes of receiving your payment your computer will receive the decryption key and return to normal.
Try anything funny and the computer has several safety measures to delete your files.
As soon as the payment is received the crypted files will be returned to normal.
Thank you
and
I want to play a game with you. Let me explain the rules:
All your files are being deleted. Your photos, videos, documents, etc...
But, don't worry! It will only happen if you don't comply.
However I've already encrypted your personal files, so you cannot access them.
Every hour I select some of them to delete permanently,
therefore I won't be able to access them, either.
Are you familiar with the concept of exponential growth? Let me help you out.
It starts out slowly then increases rapidly.
During the first 24 hour you will only lose a few files,
the second day a few hundred, the third day a few thousand, and so on.
If you turn off your computer or try to close me, when I start next time
you will get 1000 files deleted as a punishment.
Yes you will want me to start next time, since I am the only one that
is capable to decrypt your personal data for you.
Now, let's start and enjoy our little game together!
and one in Portuguese:
Eu quero jogar um jogo. Deixe-me explicar as regras:
Todos os seus arquivos serao deletados. Fotos, vídeos, documentos, etc.
Mas nao se preocupe! Só vai acontecer se voce nao cooperar.
Porém, eu já encriptei seus arquivos, entao voce nao consegue mais acessá-los.
A cada hora eu seleciono algum deles para ser excluído permanentemente,
Voce conhece o conceito de crescimento exponencial? Funciona assim:
Começa devagar e acelera depressa
Nas primeiras 24h voce só perderá alguns arquivos
No segundo dia, algumas centenas, no teceiro, milhares, e assim vai
Se voce desligar seu computador ou tentar me fechar
1.000 (MIL) arquivos serao deletados como puniçao
E voce vai querer que eu continue aqui,
já que sou o único que pode devolver seus arquivos
Agora, vamos jogar!
Envie 50 dólares (aproximadamente R$200) em bitcoins para o endereço abaixo
(Se voce nao sabe comprar e enviar bitcoins, procure no Google. É fácil)
When a victim sends a ransom payment, they can click on the check payment button. When this button is clicked, the ransomware queries the http://btc.blockr.io/ site to see if a payment has been made to the assigned bitcoin address. If the amount of bitcoins in the assigned address is greater than the payment amount, then it will automatically decrypt the files.
Update (4/12/16): Included the .KKK and .BTC extension for other variants that were discovered.
Update (4/13/16): Included the new .GWS extension, how some variants are set to start at certain times, varying prices, and the new ransom note texts.
Files associated with the Jigsaw Ransomware
%UserProfile%\AppData\Roaming\Frfx\
%UserProfile%\AppData\Roaming\Frfx\firefox.exe
%UserProfile%\AppData\Local\Drpbx\
%UserProfile%\AppData\Local\Drpbx\drpbx.exe
%UserProfile%\AppData\Roaming\System32Work\
%UserProfile%\AppData\Roaming\System32Work\Address.txt
%UserProfile%\AppData\Roaming\System32Work\dr
%UserProfile%\AppData\Roaming\System32Work\EncryptedFileList.txt
Registry entries associated with the Jigsaw Ransomware
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\firefox.exe %UserProfile%\AppData\Roaming\Frfx\firefox.exe


Comments
Nando182 - 2 years ago
Excellent work guys!!
ScathEnfys - 2 years ago
RW is getting freakier and freakier these days... would love a tech spec but I understand why you guys can't share that in the open.
Ron_ - 2 years ago
https://malwr.com/analysis/MTI0NjVkYzNlMzkyNDdiZGEwZGFhZTkyNDhkMGUxZmI/
Ron_ - 2 years ago
https://www.alienvault.com/blogs/security-essentials/building-a-home-lab-to-become-a-malware-hunter-a-beginners-guide?utm_medium=Advertising&utm_source=THN&utm_content=social
TheJokerz - 2 years ago
Great work keep it up!!
Dotcomsecurity - 2 years ago
Hello, I have for the German readers among us How to written in german language.
https://www.dotcomsecurity.de/cryptolocker-ransomware-it-security-fundamente/
Uncle_Fester - 2 years ago
Fantastic work.
AaroniusLeonius - 2 years ago
I feel like this is a kiddie coder doing this because of how easily it is decrypted. A little bit clever disguising itself as Firefox but anyone attempting to terminate it from task manager who doesn't have Firefox will likely know that is probably it. Also, people with/without Firefox who check the startup list might know it is pretending to be Firefox because who runs Firefox at startup?
ejackson - 1 year ago
Disgusting that hackers and hacker-wannabes are getting their hands on stuff like this. And while many Cryptolocker variants are appearing, efforts to combat them and discover their faults are currently underway. In this particular case for example, a vulnerability was discovered and its decryption tool was already released. In other cases it is not so easy. My recommendation is to not take any chances and get a strong anti-virus and make backups of your files. On top of that, get a powerful instant restore software like Deep Freeze or Rollback Rx to reverse any damages if the ransomware gets to infect your computer.
leksx - 1 year ago
Hello, I'm from Ukraine. yesterday removed the virus "Jigsaw" via your article . But JigSawDecrypter not " cure " all files . Please help...
Lawrence Abrams - 1 year ago
Do you still have the ransomware executable? If so, submit it to https://www.bleepingcomputer.com/submit-malware.php?channel=3 and we will get it added to the decryption tool.
Tarman - 1 year ago
"Do you still have the ransomware executable? If so, submit it to https://www.bleepingcomputer.com/submit-malware.php?channel=3 and we will get it added to the decryption tool."
I was doing exactly the instruction but still a lot of files that can not be overcome. Thank you in advance for your help
Demonslay335 - 1 year ago
Can you share a few encrypted files to that link? There may be a new version going around.
Demonslay335 - 1 year ago
Decrypter has been updated.
Demonslay335 - 1 year ago
Got the executable on channel 168, we're working on reversing it.
OrlandoFoodScene - 1 year ago
Is there any issue with removing the drive, hooking it up to another machine via a USB-SATA adapter, and decrypting the files that way? I would hate to have my clients family photos get deleted 1000 at a time simply by booting the machine if it's not necessary. Thanks for the amazing work and your time and dedication to helping out the community!
Demonslay335 - 1 year ago
(Re-posting here for future inquiries). The decrypter will work fine from another computer. Nothing from the original system is used for decryption.
OrlandoFoodScene - 1 year ago
Didn't mean to double post, but I wanted to make sure that others who ended up here could benefit from the good news! No need to boot the system to run the decrypt, so no loss of additional data! You guys are amazing! External USB adapter, here I come
Mantas12 - 1 year ago
Is Jigsaw Ransomware coded in .NET ?
Barkwolf - 1 year ago
Thanks for updating the decrypter!
myselfgg - 1 year ago
Hi Guys,
This is my first post so let me say a big Thank you to this forum.You are doing a fantastic job.
I was wondering if anybody could help me ? One of my friend got all of his files encrypted but the weird part is that the files are keeping the normal termination (.doc, .jpg etc ) but unable to open .Also no txt files or any sign of the ransomware message.
After 2 days i manage to find that it could be the jigsaw ramsomware , based on trendmicro jigsaw decryptor who saw the files as encrypted.
I did try the Jigsaw decryptor or various files with no luck .
Any help would be apreciated .
Many thanks,
Demonslay335 - 1 year ago
Have you tried identifying using ID Ransomware? You will need to upload a ransom note and encrypted file for the best chance of identification. Jigsaw ALWAYS adds an extension to encrypted files, so that is definitely not what hit your friend.
myselfgg - 1 year ago
Hi ,
Thank you for your response .
I did . As i don't have any ransom note i updated multiple files but none is recognized as Jigsaw or any other ramsomware variant. I tried every decrypt tool i could find and the only one that has seen the files as infected was Trendmicro decryptor Jigsaw, that led me to the conclusion.
Well i guess i am stuck with who knows what "mutant" version :)
Thank you for your response
Demonslay335 - 1 year ago
Most victims who have their files encrypted (in the last few months) without filename changes end up having been hit by the newer variants of PClock. You can ask your friend if the screens in the following article look/sound familiar: https://www.bleepingcomputer.com/news/security/old-cryptolocker-copycat-named-pclock-resurfaces-with-new-attacks/
myselfgg - 1 year ago
He didn't had any ransom note. he did a lot of mistakes along the way. When he realise that he can't open files he run several anti virus solution (avast , malwarebytes ).I suspect that the ransome file were deleted along with the log files.
He was installing one solution then run a full scan and after the scan he was unnistaling the solution with total unnistaler which led to no logs at all.
The only thing that looks suspicious to me is a reg file with this name USE22-1BARR-ETXGZ-HTATA-FTOGG-FTXOA.KEY in multiple folders.
Anyway, i will tell him to keep the encrypted files and to try any new decryptor that will be released.
Many thanks for your response,
Demonslay335 - 1 year ago
If you had uploaded that file to ID Ransomware, it would tell you it is Spora. Afraid there is no way to decrypt.
https://www.bleepingcomputer.com/news/security/spora-ransomware-works-offline-has-the-most-sophisticated-payment-site-as-of-yet/
myselfgg - 1 year ago
you're right it is Spora. ..:(
maybe from now he will listen my advice to backup his data
Thank you again for your time
MRLIMITLESS - 1 year ago
ive tried downloading the latest version of the jigsaw decrypter but for some reason the zip file is password protected. ive been bombed like u would not believe with the " .paytounlock " ext. it got ahold of 6 HDD's i had plugged in, ive deleted the firefox and dropbox .exe files and removed from the task manager start up section! ran dozens of anti malware scans! I cannot figure out how to decrypt it. ive checked on ID ransomware and uploaded required files, and it confirmed with me that i do hav the paytounlock jigsaw variation also told me that my files are decryptable? not having any luck. your help is much appreciated.
thankyou
( i also may possibly know where this variation originated from or where it started to spread. )
@Demonslay335
Demonslay335 - 1 year ago
If you download the decrypter and the zip file is password-protected, the password is "false-positive". This is a temporary measure due to false positives with Google.
Mobidicko - 5 months ago
Thanks for excelellent work. But i have problem with latest JIgSawDecrypter tool - 2.0.0.28 Error decrypting : "Invalid character in a Base-64 string".. Is any way to fix it? Thanks.
Demonslay335 - 5 months ago
What extension are your files? Can you share a few?
Emmanuel_ADC-Soft - 5 months ago
Hello Demonslay,
extension .blind is not only valid for the Jigsaw Ransomware.
Please check https://www.bleepingcomputer.com/forums/t/660613/need-help-in-decrypt-kill-files/
Can you please update ID Ransomware, thank you very much.
Kind regards,
Emmanuel
Emmanuel_ADC-Soft - 5 months ago
Hello Demonslay,
extension .kill is not only valid for the Jigsaw Ransomware.
Please check https://www.bleepingcomputer.com/forums/t/660613/need-help-in-decrypt-kill-files/
Can you please update ID Ransomware, thank you very much.
Kind regards,
Emmanuel
unbakedfive - 5 months ago
Hello Demonslay,
Your decrypter worked for some of my files, but a lot of them get an error that is Invalid character in a Base-64 string. Here is an example of one of the files it wouldn't decrypt:
20170510-KGW-1030HA (1).pdf.fun
Kind regards,
Tyler
Demonslay335 - 5 months ago
You need to actually share some files with me in order for me to take a look. You may PM them to me if they are possibly sensitive data.
unbakedfive - 5 months ago
https://www.dropbox.com/s/li3ddjljv8uvbuu/2014%20Master%20Price%20List.pdf.fun?dl=0
https://www.dropbox.com/s/nzj0z6vjx15v706/20170510-KGW-1030HA%20%281%29.pdf.fun?dl=0
https://www.dropbox.com/s/ekmemzx12nzgbie/Master?dl=0
Theres a few links. After running the avast decrypter the password doesn't seem to be the same for all of the files
unbakedfive - 5 months ago
That was it there was two different passwords. I used two other files and it decrypted the rest.
Demonslay335 - 5 months ago
Glad to hear you got it working. The third file isn't encrypted at all, just add the ".xls" extension.
I have fixed the bug in my decrypter, sorry about that.
Do you happen to have the ransomware executable still, or it's hash? Seems my decrypter was unable to determine a proper password for the files you sent.
unbakedfive - 5 months ago
This was the password used by avast. I don't have the executable anymore anti-virus removed it. I can also upload the unencrypted files if that would help.
0061:660E:4a95a5666990f35a51057749554e1366:00010003050300010000020006070600:5CCB15BC
podory - 5 months ago
We have a ransomware behaving like Jigsaw, but remover tool just fails to decrypt files.
Interestingly only parts of files are encrypted.
Uploaded sample (https://id-ransomware.malwarehunterteam.com) was also identified as Jigsaw and decryptable.
17 engines on Virustotal report heuristics malware. (https://www.virustotal.com/#/file/02ba43961c2db403136f903030e53f209cc91d2a6684ef108a846f28fefe2c9d/detection)
Maybe a new variant? Can it be decrypted?
Demonslay335 - 5 months ago
The malware you linked looks to just be a miner Trojan. We'd need the actual ransomware executable in order to help. What extension was added to the files?
meHorhe - 3 months ago
Hello, i got hit by some RW, not sure what, id-ransomware report 3 variants (https://id-ransomware.malwarehunterteam.com/identify.php?case=b943097dbfbdeaf9a565a7002d237e4786ba5775)
JigsawDecrypter-log: Error decrypting: Incorrect password
I have decrypted and encrypted files, but not sure about the ransom-ware executable, i hot hit through a VM and had a SharedHost with write access on the same drive. Until i finish the backup i'll not touch the VM to search for exe.
Demonslay335 - 3 months ago
It's GlobeImposter 2.0, not decryptable. The Jigsaw ID was a FP due to the extension; I've patched this.